Blog
The Vulmatch blog
-
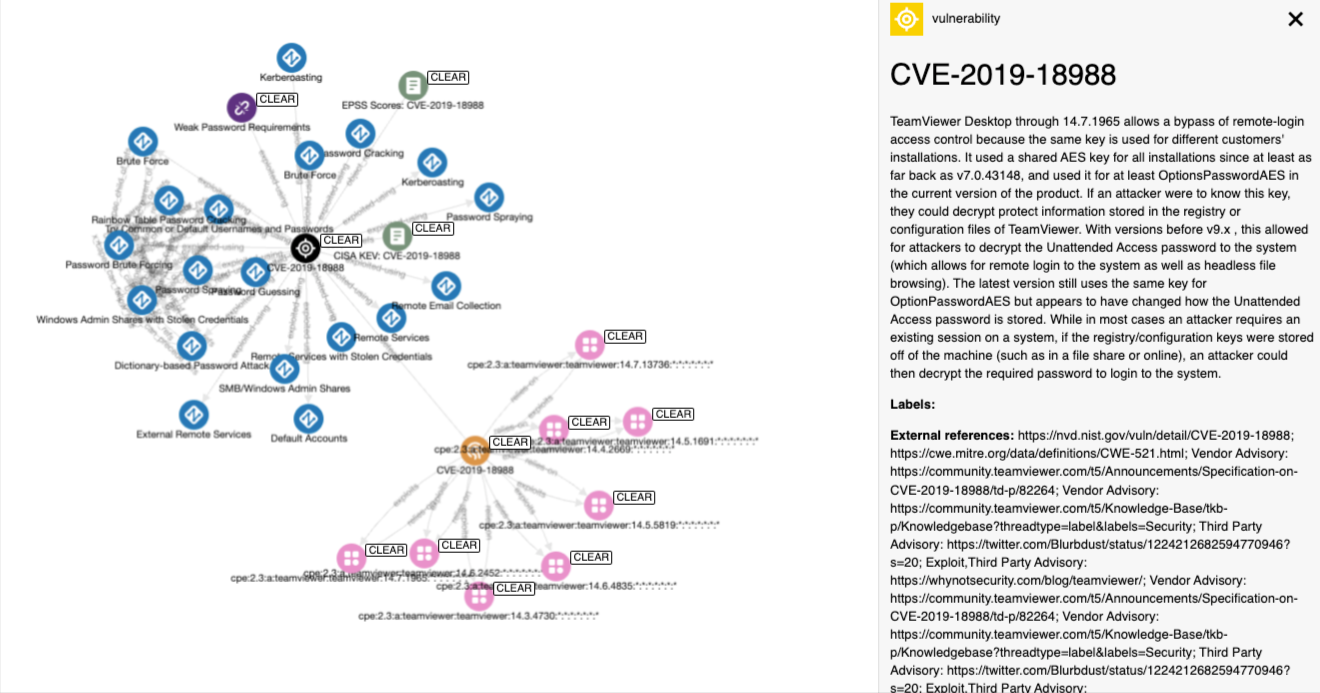
Enriching Vulnerabilities to Create an Intelligence Graph
RESEARCH December 23, 2024
We do a lot of our research into vulnerabilities. To aid this, we enrich CVEs using many remote sources of intelligence. Here is a walk-through showing how we connect CVEs to EPSS scores, CISA KEVs, MITRE ATT&CK, CWEs, and CAPECs. -
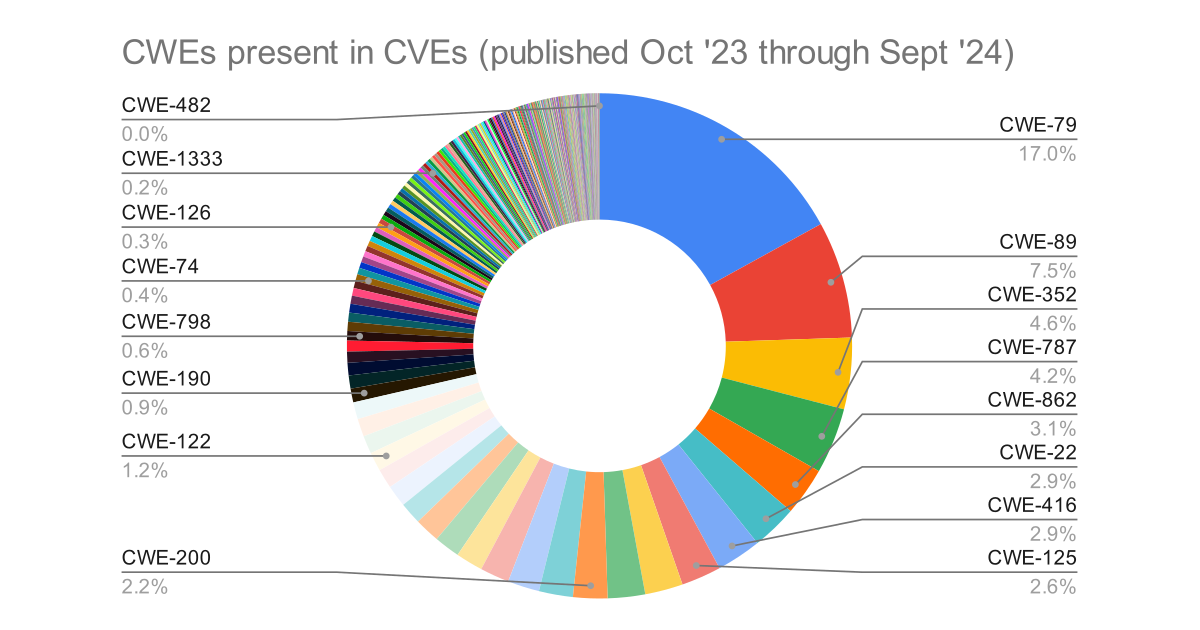
Bad Software Keeps Cyber Security Companies in Business
RESEARCH October 28, 2024
Despite countless frameworks, best practices, blog posts... so many developers still hardcode credentials into their code. -
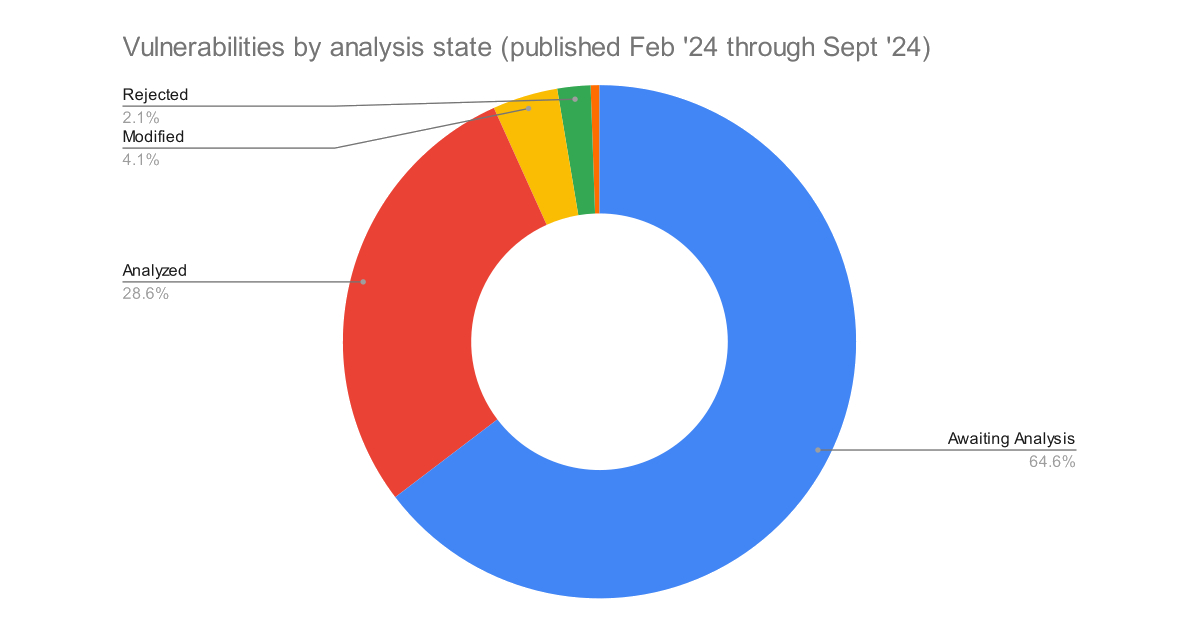
17,375 CVEs in the NVD Backlog, and Counting
RESEARCH October 07, 2024
The NVD are still struggling to keep up with the backlog of CVEs to be analysed. With 26,876 added since February, it is no surprise. -
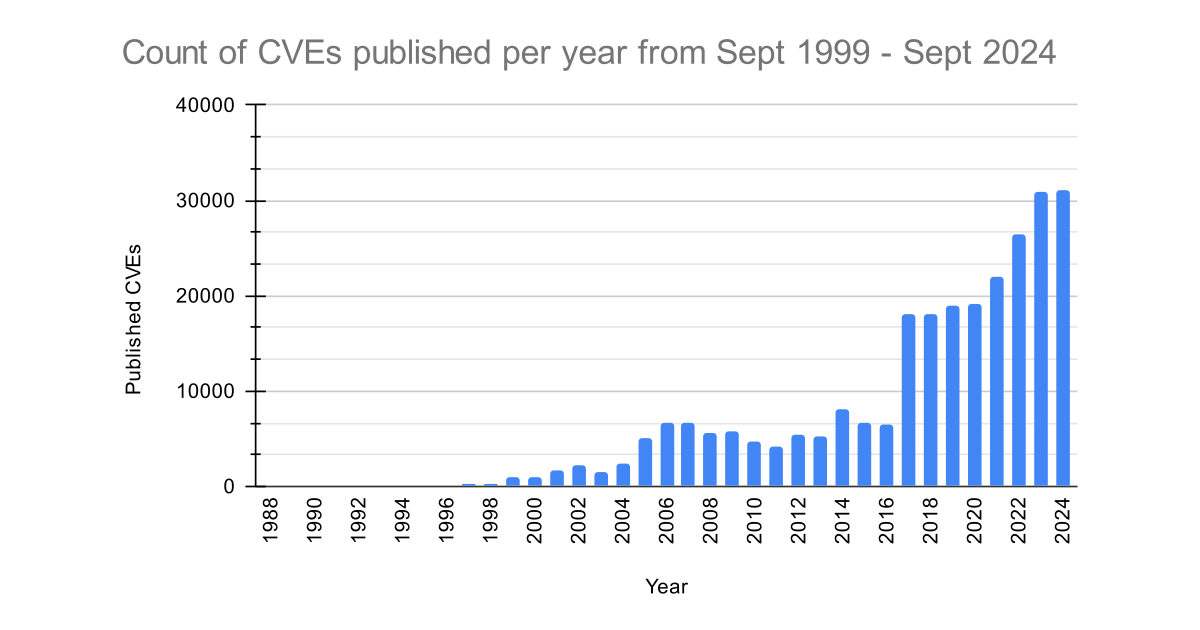
Analysing 25 Years of CVEs
RESEARCH September 30, 2024
The CVE List was launched in September 1999, listing 321 CVE records. 25 years later there are 265,767 CVE records. -
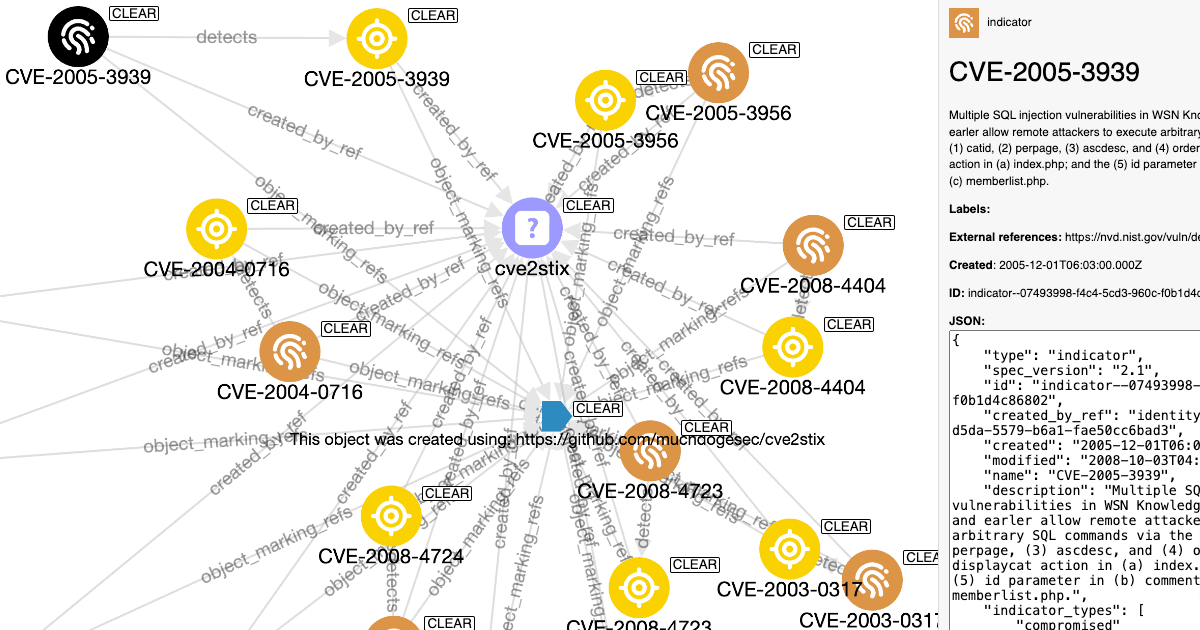
Using STIX Objects to Make Vulnerability Prioritisation Easy (and Free)
TUTORIAL September 02, 2024
Follow along as I show you how to store 200,000 CVEs as STIX objects, then use CVSS, EPSS, CISA KEV and CPE data to search and filter them. -
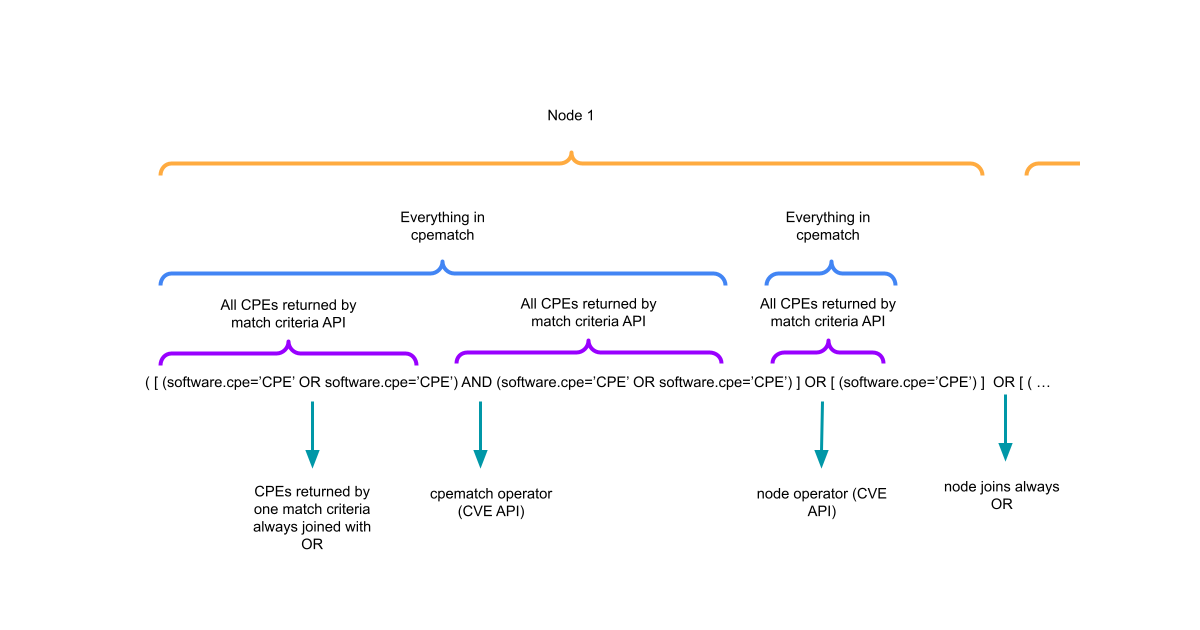
Writing Detection Rules to Identify if Products in my Stack are Vulnerable
TUTORIAL August 12, 2024
Developing on last weeks post, I show you how to construct STIX Patterns to automatically flag which products are affected by published CVEs. -
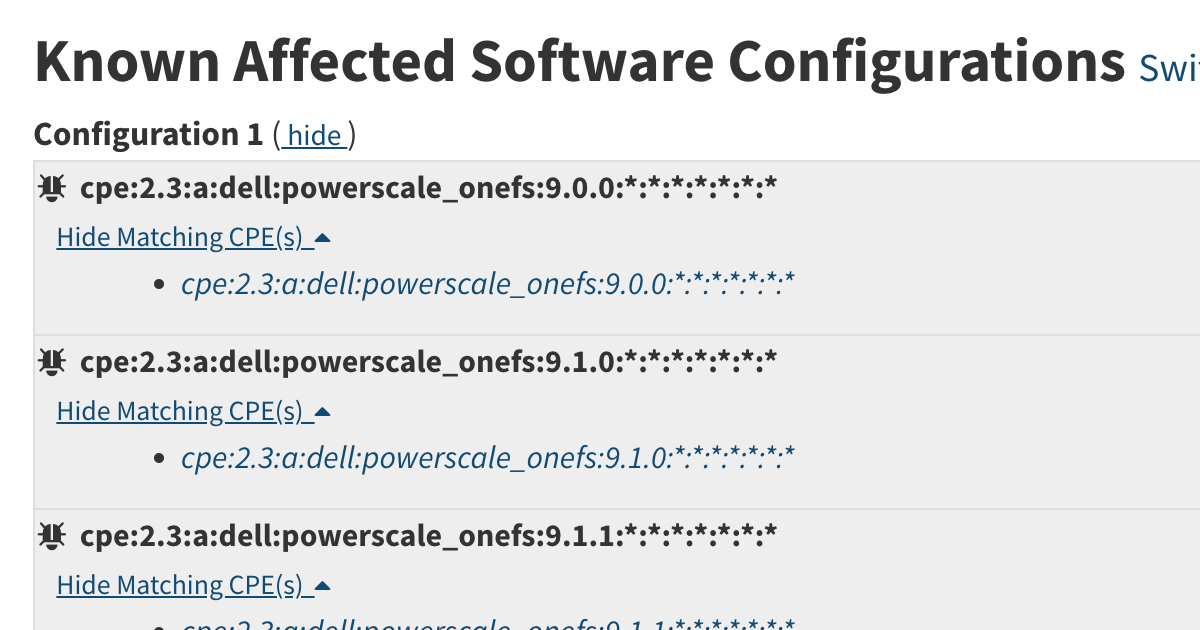
How Known Affected Software Configorations on the CVE Website are Constructed
TUTORIAL August 05, 2024
I wanted to write detection rules to identify what products are vulnerable to a CVE. In this post I walk you through my research.
